Tuesday, May 13, 2008
Interesting observation: Earthquake in China
On May 2nd, The Chaiten Volcano in southern Chile erupted with a ferocity the likes of which we've never before seen. In one days eruption it spewed out more CO2 and ash than all mankind has put in the atmosphere over the past 100 years. Mankind is pathetic when compared to the awesome power of Mother Nature. The lightning bolts alone coming out of the ash cloud is an unbelievably impressive site. But I digress...
Then the earthquake itself, at 8.0 on the Richter scale is one of the largest measured in recent history came 10 days after the volcano.
Now take a globe, put your finger on the volcano, the other on the epicenter of the earthquake and you'll notice that those two events happened on exact polar opposite ends of the earth. Spin the globe, like I did, and you'll see that it spins with PERFECT SYMMETRY.
I can only surmise that the earthquake was the recoil from the volcanic eruption, and the rainbow clouds were caused by intense disruptions in the earths magnetic field. Similar to the aurora borealis that can be seen over the North Pole It would be interesting to find out if any magnetic needles went haywire during that time... does any government body monitor earthly magnetic fields? NOAA?
Then you want to take that and double down?
Lets look at Cyclone Nargis that hit Myanmar (Burma). Burma sits on China's southern border and is the closest neighbor to the earthquake region. Well; the cyclone hit on the same day that the volcano was erupting, on May 2nd.
Now this may all be coincidence, sure. But it could be argued, and in fact I do hereby put forth the argument that the pending eruption in Chile caused disruptions in the earths magnetic field, which then helped create the low pressure area over the Bay of Bengal which spawned cyclone Nargis.
Now lets go ALL IN, shall we?
Connect the dots. Start at the epicenter of the earthquake and draw a line to where the cyclone made landfall on the coast of Myanmar (Burma). Continue to draw your line along the path (trajectory) that the cyclone followed as it picked up steam, take that line all the way back to the origins of the storm (which the US Navy called "tropical cyclone #95b") Then continue to draw that line to meet up with the Chaiten Volcano. Now take a look at the shape you just drew... it is a perfectly straight line.
The line covers spans a massive 11,000 miles of ocean without a single continent getting in the way. From Chile to the South Atlantic Ocean, past the southern tip of Africa and over the Indian Ocean, maintaining the course all the way up to the Bay of Bengal, to the coast of Myanmar where the cyclone made landfall and on up to the epicenter of our 8.0 earthquake.
Thursday, March 13, 2008
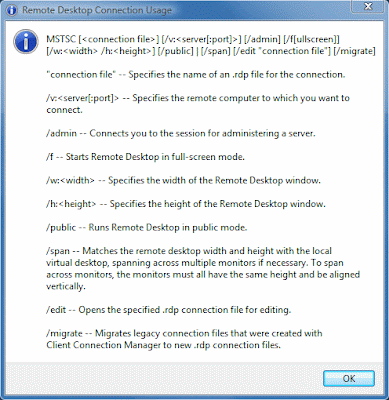
Vista Remote Desktop Command Line Options
Windows Vista SP1 installs MSTSC.exe version 6.0.6001.18000 on to your computer, the only way to discover this information is to browse to the MSTSC.exe file in explorer which is located in the c:\windows\system32\ directory. Right click on MSTSC.exe and select properties, then select the "Details" tab
You can find all these startup commands by running "MSTSC /?" from the run command, and because Microsoft in all their wonder only outputs this data in a screen where you cannot copy the text from (unless you know the trick) I have posted the output here for you to use as you see fit.
OUTPUT FROM MSTSC /? Command:
MSTSC [
"connection file" -- Specifies the name of an .rdp file for the connection.
/v:
/admin -- Connects you to the session for administering a server.
/f -- Starts Remote Desktop in full-screen mode.
/w:
/h:
/public -- Runs Remote Desktop in public mode.
/span -- Matches the remote desktop width and height with the local virtual desktop, spanning across multiple monitors if necessary. To span across monitors, the monitors must all have the same height and be aligned vertically.
/edit -- Opens the specified .rdp connection file for editing.
/migrate -- Migrates legacy connection files that were created with Client Connection Manager to new .rdp connection files.
Monday, October 29, 2007
Our Broken Itelligence Agencies
Human Intelligence, CIA
Signal Intelligence, NSA
The English have been masters at the spy trade for centuries. In WWII, the United States felt that it should get into the act and turned to the English for guidance.
With their tutelage, the CIA became a formidable tool against the Soviet threat throughout the cold war. We had clearly defined enemies with clearly defined borders. Gathering intelligence became a methodical science... then, once the Soviet Union collapsed, the clearly defined enemies with clearly defined borders went with it.
The growth of the internet created an atmosphere wherein information and 'intelligence' became a commodity. Then the emergence of an enemy that is not only difficult, if not impossible, to clearly define but who also operates entirely without borders. The polar opposite from what the CIA were trained to do.
The CIA knew about al Qaeda operators operating in the USA prior to 9/11, yet did nothing to notify the FBI. This is because of the opposing nature of each agency. The CIA finds a criminal and wants to string them along to see what intelligence they can uncover by monitoring them. When the FBI finds a criminal, they want to string them up. From the CIA perspective, the FBI sure knows how to screw up an investigation and destroy your intelligence network.
Monday, October 22, 2007
No Rules, Just Write - and the OLPC
Anywhere that you have connectivity combined with the absence of a functioning judicial system; you will breed crime. It doesn't matter what that connectivity is, or how you measure that connectivity - whether it is in paved roads, running water, electricity - each of these factors contributes to both the reach of commerce and the reach of criminals. The two cannot be divorced from each other. If you have a rapid expansion of transportation, without an equal expansion of police power, criminals will exploit that weakness. In the wild west, outlaws would rob trains as they crossed the nation, knowing that they'd be vulnerable and there was little chance of being caught.
Let's look at Russia. Back in the cold war era, there were technology export restrictions in place. With the fall of the Iron Curtain, those restrictions were relaxed. By the time we in the United States started going online en-masse in 1995, upgrading our computer systems to Pentium machines running Windows 95 - our old computer systems didn't go into the garbage, they were sold into the huge technological vacuum of the former Soviet Union.
Who are the early adopters of technology? Kids of course! And Russia was no exception. Like a 16-year-old with a hot rod, the youths started souping up computers that we considered garbage. They got on to the internet using whatever they could, and once they connected to our information flows, they started teaching themselves programming. Because they were learning to program on outdated equipment, this forced them to become very, very good. There was no such thing as code bloat. Then you add 5 years to the calendar and what do you have? Little Ivan is no longer 15, he is 20 and has 5 years experience - and therein lies the rub - Ivan cannot go out and get a job in information technology, there is no economy to support his skill set. So, he goes about earning a living any way he can. I call it "N0 RUL3Z, JU5T WR1T3". Ivan sets about writing spam software, creating Trojan horses, worms... this is where we see the emergence of the botnet.
Brazil wasn't far behind. In 2004-2005 we saw an uptick in the botnet wars arms race with Russia being one-upped by Brazil with the Beagle/Bagle, Mydoom and Sasser botnet pissing contest.
There is a tide shift taking place. Putin has implemented a 12% flat tax which is bringing revenues flowing into the Russian economy for the first time in 15 years. They are reviving their legal system because they want to attract the Foreign Direct Investment dollars which will never come if they have no legal system which can enforce a legal contract. Along with the civil justice and FDI dollars, criminal justice must reign in corruption otherwise the FDI dollars will quickly disappear. So, Russia is growing out of the script kiddie phase and reemerging onto the world scene. Its good to have Mother Russia back (New & Improved with 1337 h4x0rs).
I could go on providing details of history and economics, but I will leave that for the book I'm writing. But I will pose this question for you to think about: What do you think the outcome of One Laptop Per Child will have on the future of cybercrime? If connectivity absent a legal system is the breeding ground for crime, what do you think will happen as the bottom billion in Africa gets online?
Computer security is all about dealing with the unintended consequences. Every computer and every system that was ever built was first done to share information, not secure it. Security only came after we got everything connected, then had the collective "awww crap!" moment.
Thursday, August 30, 2007
Global Policy Changes
Financial Services Firms Simulate Flu Pandemic
The U.S. Government is co-sponsoring a three-week exercise that will simulate the impact of a flu pandemic on financial services firms, including their ability to support telecommuters. The exercise is expected to be the largest in U.S. history and will involve more than 1,800 firms. From the article: 'The program will follow a compressed time frame that simulates the impact of a 12-week pandemic wave. Participants will be given information on how many absentee employees they can expect. Companies won't know exactly how hard they will be hit with sick-calls from employees until this data is made available ... In addition, participating firms won't be able to pick and choose the level of workforce reductions they get hit by.I think you might be very surprised at how much value comes out of running these types of simulations. I work in the tech field and that side of the story is easy to imagine but as I worked with economists and academia it gave me a new appreciation that I would like to share with you.
Pre-Y2k, the government wanted to plan for the "Systemic Perturbations" that could come out of the Y2k bug. The US Gov't said to its top economists, military leaders: "Assume it is going to be bad, the worst case scenario." For once, perhaps the first time in history, we knew beforehand WHAT the vertical shock to the system was going to be and on what date and time it was going to happen. This gave the discussion a very real sense of importance because it wasn't hypothetical. In disaster planing, you don't know what the vertical shock is going to be-- think of a rock hitting a pond, you don't know how big the rock will be or when, where it will hit, and from a planning scenario it doesn't matter because what you need to plan for is how to deal with the huge splash it creates and the waves and ripples it creates. Once you have created plans to deal with the splash and ripples, what they term as "System Perturbations" you are then ready for any vertical shock (rock hitting pond) to the system. The rock can hit anywhere and be any size. We already know how to respond to the splash and run all the ripples to ground.
So, with Y2k, the Pentagon engaged with a global financial firm of Cantor Fitzgerald to plan for the vertical shock of Y2k and what sort of rule set resets are going to take place. If Y2k was going to be big, Banks failing, power outages, trading stops, mass chaos, martial law... what would be the GLOBAL impact of such massive chaos. Interestingly, Cantor Fitzgerald stated: "I think we've seen this before, in China, with SARS."
Huh? What does China and SARS have to do with Y2k bug?
The Chinese healthcare system, and by extension their entire government was very closed about revealing any of their internal problems. When the SARS outbreak happened, Chinese authorities ignored the problem. When SARS started spreading, the World Health Organization (WHO) started inquiring with China about the outbreaks and extent of the spread within China. China flat denied that any problem existed. When people started dying, the WHO shut down all flights leaving certain Chinese provinces suspected of spreading SARS. This had a DIRECT impact on the Chinese economy and government.
The Chinese immediately responded. "AH, roo mean SARS! Well, we have very much SARS!" To this day, there are police stationed at the airport that will approach any passenger and take their temperature on the spot. If you are running a fever, or you don't look 100% healthy, you don't fly. You've just won an extended 3 day vacation with all expenses paid by YOU because they don't ever want to run the risk of spreading disease and having their airports shut down again. This also started the Chinese equivalent of the CDC to start cooperating with the WHO, which is why we know about the H5N1 "Bird Fru" virus years before it has become a viable threat to humans.
The real lesson here was this: China received a vertical shock to their system. The direct result of that shock was rapid changes taking place to China's political system, changes that NEVER could have come about on their own absent the external influence. An external event causing internal change. Internal change that never could have come internally. Rapid policy changes that forever alter the way the country interacts with the outside world. This was huge.
The correlation to Y2k was the recognition that the vertical system shock to the global system would create unheard of system perturbations. The output of which would cause a permanent global policy change that would forever alter the rules by which governments interact with each other and how each government interacts with its own citizens. External events driving internal change.
Well, as we all know, on 01 January 2000 at 00:00:01 hrs: nothing happened. There was no vertical shock. We planned for the worst and the best happened, with the possible exception of the ten million pissed off network administrators that spent the party of the century sober watching server lights blink.
Then, a year and nine months later, something did happen. 11 September 2001 was a huge vertical shock to the global system. The result of which caused massive global policy change that forever altered the rules by which governments interact with each other and how each government interacts with its own citizens. For the first year after, every day you could pick up the paper and read about a NEW law being passed or policy being implemented that would forever change business-as-usual. To this day, you read any newspaper and you'll see some story that can be traced back to that event. It was a massive global rule set reset. It could be said that the reason that the USA recovered so well from 9/11 was a direct result of the system shock and perturbations that were planned for on Y2k.
Second major lesson was that you cannot predict the vertical shock, but you can plan for the horizontal output and how you'll run those situations to ground.
So, the impact on Information Technology is simply a very small, yet very important sub-component of these war games.
Tuesday, August 21, 2007
Wells Fargo Bank Offline - 48 hours and counting
They issued a press release yesterday, stating that they had experienced a "service disruption", an excuse that worked yesterday. Today, I want answers.
Where is my money? Is it safe? Can I access it?
I monitor the activities of online criminals, primarily Russians. In visiting their online forums, they're speculating what the problem is, but what they're really doing is gearing up for a massive phishing run unlike any other seen before. The criminals have now amassed databases of "fulls", a term they use to indicate they have the targets full personal information, all they need is access to the online banking.
Their increased sophistication is evident in the emails they're crafting for this scam.
=====================
Dear {firstname} {lastname},
Your primary email address for Wells Fargo Bank Online has been successfully changed.
Thank you for using Wells Fargo Bank Online Services
Save time and money by paying your bills online. Its safe, secure and easy to set up. For more information sign in to online banking center and click the 'Bill Pay' tab.
=====================
And that's it... this email combined with other tried and true techniques are sure to catch a few phish. Adding injury is that Wells Fargo customer service is already swamped with complaints, is going to be playing catch-up with millions of delayed transactions, and is sure to let transactions through and deal with the consequences later.
I will provide updates as this situation unfolds. The problem is already big, and its going to get a whole lot worse.
Joel Helgeson
Monday, July 30, 2007
U//FOUO
The average Joe Sixpack now has access to more information than ever before. What we don't have, and don't need to have access to is the ops intel that comprises the majority of classified intel today. e.g. On 9/11/01, when President Bush was airborne, the press speculated about the location of Vice President Cheney. Many in the press speculated that he was being hidden away in the bunkers beneath the White House. While they may have been correct, Cheney's actual location was classified. The press could speculate all they wanted, the Secret Service would not reveval anything other than he was safe. Had any SS agent come out and confirmed his location, that would have been disseminating classified information.
